Data breaches management plans are becoming more frequent, impacting businesses of all sizes. These breaches expose sensitive information and can occur through hacking, phishing, or human errors. The damage can be severe, affecting both the business and its customers.
Without a plan, the impact of a breach can spiral out of control, leading to legal issues, financial losses, and reputational harm.
This is where a Data Breach Management Plan is essential. It guides you in detecting, stopping, and recovering from breaches. The plan helps you minimise damage and quickly restore your business operations.
What is Data Breach Management?
A Data Breach Management Plan is like a guide for handling data breaches. It covers everything:
- Finding the breach
- Stopping it
- Notifying affected people
- Taking steps to prevent it from happening again
This plan helps reduce confusion during a breach and ensures your business can quickly return to normal.
Why You Need a Data Breach Management Plan:
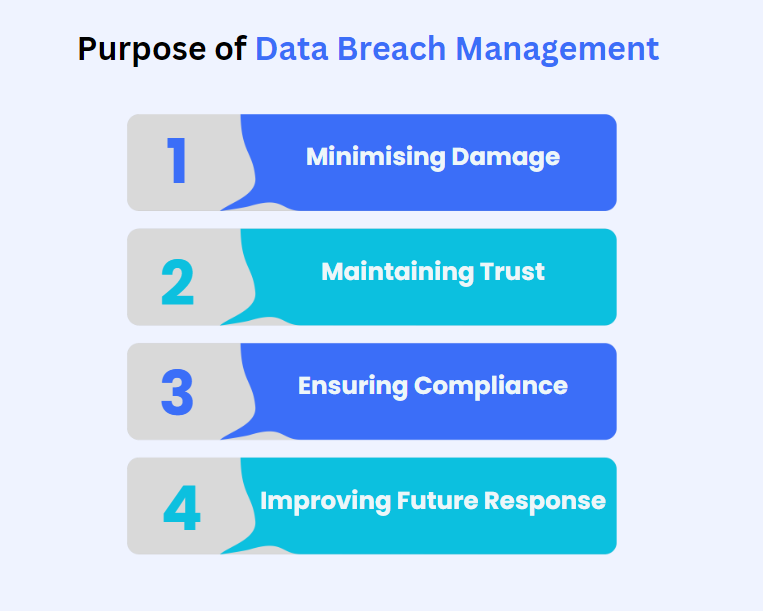
- Minimising Damage
Taking quick action limits the impact on both your business and your customers.
It’s like fixing a small leak before it turns into a flood. - Maintaining Trust
How you handle a breach affects your reputation.
Being open and managing the situation well helps keep your customers’ trust. - Ensuring Compliance
Following legal requirements (like GDPR, CCPA) avoids fines and legal trouble.
It’s about following the rules and protecting your business. - Improving Future Response
Each breach teaches you something new.
By reviewing what happened, you can strengthen your future responses and reduce the risk of it happening again.
Cyber vs. Non-Cyber Breaches:
There are two main types of breaches:
- Cyber Breaches involve attacks on your digital systems, such as hacking or malware. They require specific management tools and strategies.
- Non-cyber breaches include stolen physical documents or unauthorised access to files. Although they don’t involve computers, they still need careful handling.
16 Key Steps to Develop Your Data Breach Management Plan
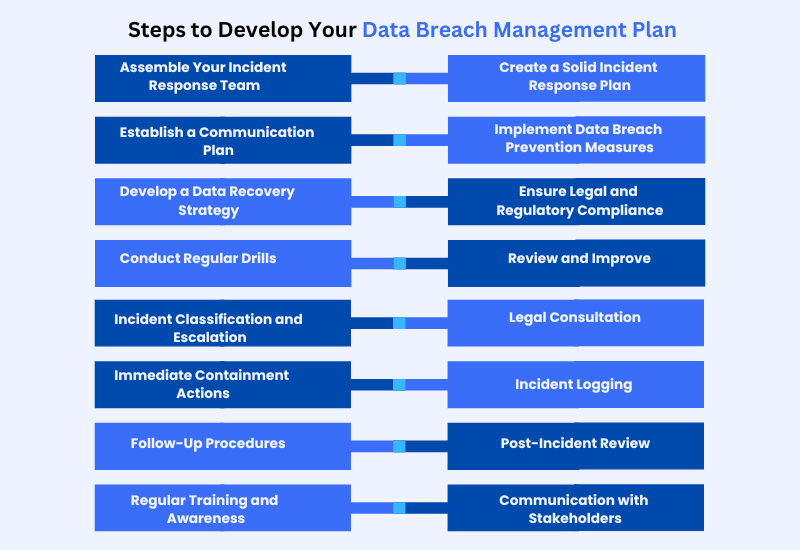
Assemble Your Incident Response Team
Think of your team as the Avengers of data protection. Gather key people from IT experts, PR managers, legal advisors, and more. Each person should know exactly what to do in an Incident Response Plan. Regular training is crucial to ensure everyone is prepared to jump into action.
Create a Solid Incident Response Plan
This is the backbone of your strategy. Your Incident Response Plan should outline every possible step from detection to resolution. Ensure it’s thorough but flexible enough to handle different types of breaches. It’s about being prepared for anything while staying adaptable.
Establish a Communication Plan
Good communication can turn a potential PR disaster into a controlled response. Develop a Data Breach Communication Plan to handle internal and external communication. This includes informing affected individuals, notifying regulatory bodies, and managing media relations. Your communication should be prompt, clear, and consistent.
Implement Data Breach Prevention Measures
Invest in Data Breach Prevention strategies. Use tools like security audits, up-to-date software and employee training to reduce the chances of a breach.
Develop a Data Recovery Strategy
When a breach occurs, you need a solid data breach recovery plan. This plan should detail restoring systems and data, minimising disruption to your operations so you can get back on track quickly and smoothly.
Ensure Legal and Regulatory Compliance
Ensure your plan covers Data Breach Compliance with laws like GDPR or CCPA. This includes understanding Breach Notification Requirements and ensuring your actions align with legal obligations.
Conduct Regular Drills
Just like fire drills, breach drills are essential. Regularly test your Incident Management Framework to ensure your response plan works under pressure. These drills help you identify gaps and make necessary improvements.

Review and Improve
After handling a breach, take time for a thorough review. Review what went right and what didn’t. Use this information to refine your Breach Management Strategies and update your plan. Continuous improvement can make your plan stronger for future challenges.

Incident Classification and Escalation
Classify the breach based on severity and type. This will guide the response and determine if escalation is needed. Quick identification and escalation can help contain the breach effectively.
Legal Consultation
Consult legal experts to confirm your response complies with legal and regulatory standards. This step is vital for managing risks and preventing legal complications.
Immediate Containment Actions
Implement quick actions to contain the breach and prevent further damage. This includes isolating affected systems and limiting the breach’s impact.
Incident Logging
Document all details related to the breach, including timelines and actions taken. This record will be valuable for audits, reviews, and future improvements.
Follow-Up Procedures
Address any identified vulnerabilities to prevent future breaches. Update security measures and improve response strategies.
Post-Incident Review
Conduct a detailed review after the breach to identify lessons learned and improve your response plan. This will help refine your strategies and prevent future incidents.
Regular Training and Awareness
Keep your team updated with regular training and awareness programs. Continuously inform them about best practices and emerging threats to ensure they stay prepared.
Communication with Stakeholders
Maintain open lines of communication with stakeholders, including customers, partners, and regulators. Provide updates and manage their expectations to keep everyone informed.
5 Pro Tips for Effective Data Breach Management

- Stay Informed and Educated
The world of cyber threats is constantly changing. Stay updated on threats and best practices by attending webinars, reading blogs, and continuing your learning. Knowledge is your best defence against breaches. - Invest in Robust Security Tools
Don’t skimp on security tools. Use advanced solutions for threat detection and prevention. Consider encryption, intrusion detection systems, and secure access controls. These tools are like your armour against cyber threats. - Maintain Clear Documentation
Keep detailed records of all breach-related activities. This includes everything from the initial detection to the final recovery steps. Clear documentation helps in audits and can be crucial to prove compliance. - Foster a Culture of Security Awareness
Your team is your first line of defence. Foster a security culture by regularly reminding employees of best practices and encouraging them to report suspicious activities. - Engage with Experts
Sometimes, you need a little extra help. Consult with cybersecurity professionals to enhance your Data Breach Management Plan. Their expertise can provide valuable insights and help you fine-tune your strategies.
Conclusion
A Data Breach Management Plan is more than a legal requirement—it’s an essential component of your organisation’s risk management strategy. By following these steps and tips, you’ll be better prepared to handle data breaches efficiently and effectively. By preparing ahead, communicating clearly, and constantly improving, you’ll be ready to handle breaches effectively and get back to business fast.
